Table of Contents
Intel® EPID is a cryptographic protocol which enables the remote authentication of a trusted platform whilst preserving the user's privacy.
Roles
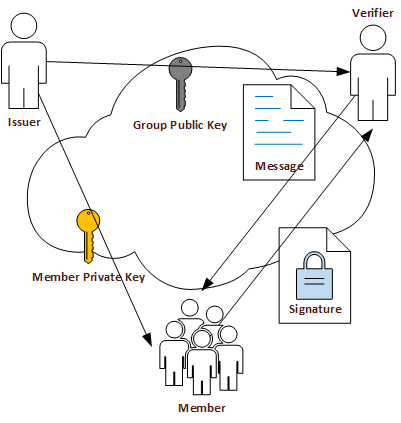
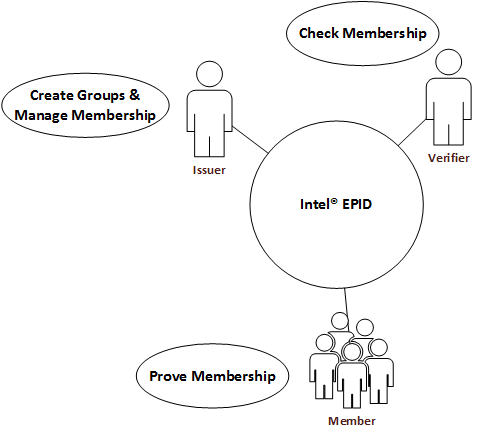
In the Intel® EPID scheme, there are three roles: issuers, members, and verifiers.
The entities in these roles interact with each other in such a way that a member can prove to a verifier that it is a trusted member of a group without disclosing the identity of the member. Groups are created and managed by the issuer.
Issuers
The issuer is responsible for managing group membership.
The issuer manages groups by doing the following:
- Creates groups by generating one issuing private key and one group certificate for each group. The group certificate contains the group public key.
- Creates group members by generating unique Intel® EPID member private keys through bulk provisioning. Member private keys are created from the issuing private key for the group.
- Manages requests from prospective members to join existing groups by using the join protocol.
- Creates and maintains signature based revocation lists and private key based revocation lists. These lists of members no longer in good standing allow members to be dropped from a group.
- Creates and maintains group revocation lists.
- Makes group public keys and revocation lists available to verifiers.
Members
The member is the entity that attempts to anonymously prove its group membership to the verifier.
- Members are authorized by the issuer as part of a group.
- Each group member has a unique Intel® EPID private key, which corresponds to the group.
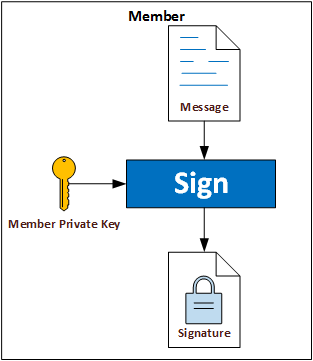
- The member uses its member private key to sign a message to prove group membership to the verifier without revealing the identity of the member.
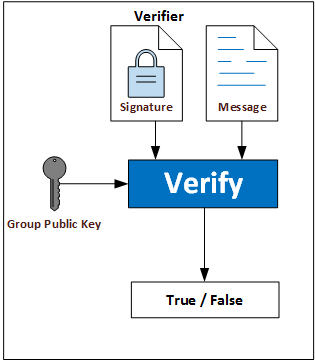
Verifiers
The verifier checks an Intel(R) EPID signature to establish whether it was signed by an entity or device that is a member in good standing.
The verifier acts on behalf of a party that needs to know it is communicating with a trusted device. Verifiers obtain group certificates and revocation lists from issuers and negotiate details of signature protocol with members.
A verifier can do the following:
- Confirm a member is in fact a member of a given group in good standing.
- Obtain group certificates and revocation lists from issuers.
- Negotiate details of signature protocol with members.
Groups
An Intel® EPID group represents a set of trusted entities called members. Issuers create groups and manage group membership. For each group, the issuer creates a group public key simultaneously with the corresponding issuing private key. The issuer uses the issuing private key to create unique member private keys for each group member, and makes the group public key available to verifiers.
All groups have the following:
- Group public key, which corresponds to the issuing private key kept by the issuer
- Signature based revocation list
- Private key based revocation list
- Member private keys, generated from the issuing private key
If a signature based revocation list or private key based revocation list does not exist, it is assumed to be empty.
Keys
The Intel® EPID scheme works with three types of keys: the group public key, the issuing private key, and the member private key. A group public key corresponds to the unique member private keys that are part of the group. Member private keys are generated from the issuing private key.
Additionally, in the Intel® EPID scheme, a private key can be revoked given a signature created by that key, even if the key itself is still unknown. Group membership can be revoked and entire groups can be revoked. For more information on revocation, refer to Revocation.
Group Public Key
The group public key is the key used by the verifier to confirm that a member belongs to a group in good standing. Each member private key in a group is associated with the group's public key.
When a group is created, the group public key and the issuing private key are simultaneously generated by the issuer. The verifier obtains the group public key from the issuer.
Issuing Private Key
The issuing private key is the key used by the issuer to generate unique private keys for each member of a given group. For every group public key, there is a corresponding issuing private key. The issuing private key remains with the issuer and is kept private.
Member Private Key
The member private key is the key used by the member to digitally sign a message when attempting to prove to the verifier that the member belongs to the group and is in good standing.
Unique member private keys are generated by the issuer for each member of a given group. The same group public key corresponds to each member private key in the group.
Member and Verifier Interaction
Each Intel® EPID member uses its Intel® EPID private key to digitally sign a message. The resulting signature is called an Intel® EPID signature.
The Intel® EPID verifier uses the group public key to verify the correctness of an Intel® EPID signature, i.e., to verify that the signature was indeed created by a member with a valid Intel® EPID private key.
However, the Intel® EPID signature does not convey any information about which unique private key was used to create the signature.